Transport Layer Security | tls vs ssl
Network security involves getting information against assaults while it is on the way on an organization. To accomplish this objective, some constant security conventions have been planned. There are well known norms for constant organization security conventions like S/Emulate, SSL/TLS, SSH, and IPsec. As referenced before, these conventions work at various layers of systems administration model.
In the last section, we examined a few famous conventions that are intended to give application layer security. In this part, we will examine the most common way of accomplishing network security at Transport Layer and related security conventions.
For TCP/IP convention based network, physical and information connect layers are regularly carried out in the client terminal and organization card equipment. TCP and IP layers are carried out in the working framework. Anything above TCP/IP is carried out as client process.
Need for Transport Layer Security
We should examine an ordinary Web based deal.
Sway visits Alice's site for selling products. In a structure on the site, Sway enters the kind of good and amount wanted, his location and installment card subtleties. Sway taps on Submit and hangs tight for conveyance of merchandise with charge of cost sum from his record. This sounds great, however without any organization security, Weave could be in for a couple of shocks.Transport Layer Security
●On the off chance that exchanges didn't utilize secrecy (encryption), an aggressor could get his installment card data. The aggressor can then make buys to Bounce's detriment.
●Assuming that no information honesty measure is utilized, an aggressor could alter Weave's structure with regards to type or amount of products.
●Ultimately, in the event that no server confirmation is utilized, a server could show Alice's renowned logo yet the site could be a vindictive site kept up with by an assailant, who is taking on the appearance of Alice. Subsequent to accepting Weave's organization, he could take Sway's cash and escape. Or on the other hand he could do a data fraud by gathering Sway's name and charge card subtleties.
Transport layer security plans can resolve these issues by upgrading TCP/IP based network correspondence with classification, information uprightness, server validation, and client confirmation.
The security at this layer is for the most part used to get HTTP put together web exchanges with respect to an organization. In any case, it very well may be utilized by any application running over TCP.
Theory of TLS Plan
Transport Layer Security (TLS) conventions work over the TCP layer. Plan of these conventions utilize well known Application Program Points of interaction (Programming interface) to TCP, called "attachments" for communicating with TCP layer.Transport Layer Security
Read more: network security keyNetwork Security – Application Layer
Applications are presently interacted to Move Security Layer rather than TCP straightforwardly. Transport Security Layer gives a basic Programming interface attachments, which is comparative and closely resembling TCP's Programming interface.
Theory of TLS Plan
In the above chart, in spite of the fact that TLS actually lives among application and transport layer, according to the normal point of view a vehicle convention goes about as TCP layer upgraded with security administrations.
TLS is intended to work over TCP, the dependable layer 4 convention (not on UDP convention), to make plan of TLS a lot less difficult, in light of the fact that it doesn't need to stress over 'timing out' and 'retransmitting lost information'. The TCP layer keeps doing that as expected which serves the need of TLS.
Why TLS is Well known?
The justification behind prevalence of utilizing a security at Transport Layer is straightforwardness. Plan and arrangement of safety at this layer requires no adjustment of TCP/IP conventions that are executed in a working framework. Just client cycles and applications should be planned/altered which is less intricate.
Secure Attachment Layer (SSL)
In this segment, we examine the group of conventions intended for TLS. The family incorporates SSL adaptations 2 and 3 and TLS convention. SSLv2 has been currently supplanted by SSLv3, so we will zero in on SSL v3 and TLS.
Brief History of SSL-Transport Layer Security
In year 1995, Netscape created SSLv2 and utilized in Netscape Guide 1.1. The SSL version1 was rarely distributed and utilized. Afterward, Microsoft refined SSLv2 and presented another comparable convention named Private Interchanges Innovation (PCT).
Netscape considerably further developed SSLv2 on different security issues and conveyed SSLv3 in 1999. The Web Designing Team (IETF) consequently, presented a comparative TLS (Transport Layer Security) convention as an open norm. TLS convention is non-interoperable with SSLv3.
TLS adjusted the cryptographic calculations for key extension and validation. Likewise, TLS proposed utilization of open crypto Diffie-Hellman (DH) and Advanced Mark Standard (DSS) instead of protected RSA crypto utilized in SSL. In any case, because of expiry of RSA patent in 2000, there existed no really great explanations for clients to move away from the broadly sent SSLv3 to TLS.
Remarkable Highlights of SSL
The remarkable highlights of SSL convention are as per the following −
●SSL gives network association security through −
○Classification − Data is traded in an encoded structure.
○Confirmation − Correspondence substances recognize each other using computerized declarations. Web-server confirmation is compulsory though client validation is kept discretionary.
○Dependability − Keeps up with message respectability checks.
●SSL is accessible for all TCP applications.
●Upheld by practically all internet browsers.
●Furnishes ease in working with new web-based elements.
●Grown basically for Web internet business.
Design of SSL
SSL is well defined for TCP and it doesn't work with UDP. SSL gives Application Programming Connection point (Programming interface) to applications. C and Java SSL libraries/classes are promptly accessible.
SSL convention is intended to interwork among application and transport layer as displayed in the accompanying picture −
SSL Design-Transport Layer Security
SSL itself is certainly not a solitary layer convention as portrayed in the picture; as a matter of fact it is made out of two sub-layers.
●Lower sub-layer includes the one part of SSL convention called as SSL Record Convention. This part gives uprightness and classification administrations.
●Upper sub-layer involves three SSL-related convention parts and an application convention. Application part gives the data move administration between client/server connections. Actually, it can work on top of SSL layer also. Three SSL related convention parts are −
○SSL Handshake Convention
○Change Code Spec Convention
○Ready Convention.
●These three conventions deal with SSL message trades and are all talked about later in this part.
Elements of SSL Convention Parts
The four sub-parts of the SSL convention handle different undertakings for secure correspondence between the client machine and the server.
●Record Convention
○The record layer arranges the upper layer convention messages.
○It sections the information into sensible blocks (max length 16 KB). It alternatively packs the information.
○Scrambles the information.
○Gives a header to each message and a hash (Message Verification Code (Macintosh)) toward the end.
○Surrenders the organized blocks to TCP layer for transmission.
●SSL Handshake Convention
○It is the most perplexing piece of SSL. It is summoned before any application information is communicated. It makes SSL meetings between the client and the server.
○Foundation of meeting includes Server validation, Key and calculation exchange, Laying out keys and Client confirmation (discretionary).
○A meeting is distinguished by remarkable arrangement of cryptographic security boundaries.
B○Numerous protected TCP associations between a client and a server can have a similar meeting.
B○Handshake convention activities through four stages. These are examined in the following segment.
ChangeCipherSpec Convention
●Least difficult aspect of SSL convention. It involves a solitary message traded between two imparting elements, the client and the server.
●As every substance sends the ChangeCipherSpec message, it changes its side of the association into the safe state as settled upon.
●The code boundaries forthcoming state is duplicated into the present status.
●Trade of this Message shows generally future information trades are scrambled and honesty is safeguarded.
●SSL Ready Convention
○This convention is utilized to report mistakes -, for example, startling message, awful record Macintosh, security boundaries exchange fizzled, and so on.
○It is additionally utilized for different purposes -, for example, inform conclusion of the TCP association, advise receipt of awful or obscure testament, and so on.
Foundation of SSL Meeting-Transport Layer Security
As talked about above, there are four periods of SSL meeting foundation. These are principally dealt with by SSL Handshake convention.
Stage 1 − Laying out security abilities.
●This stage contains trade of two messages - Client_hello and Server_hello.
●SSL Meeting Foundation Phase1
●Client_hello contains of rundown of cryptographic calculations upheld by the client, in diminishing request of inclination.
●Server_hello contains the chose Code Determination (CipherSpec) and a new session_id.
●The CipherSpec contains fields like −
○Figure Calculation (DES, 3DES, RC2, and RC4)
○Macintosh Calculation (in light of MD5, SHA-1)
○Public-key calculation (RSA)
○The two messages have "nonce" to forestall replay assault.
Stage 2 − Server confirmation and key trade.
SSL Meeting Foundation Phase2
●Server sends authentication. Client programming comes designed with public keys of different "trusted" associations (CAs) to really look at testament.
●Server sends picked figure suite.
●Server might demand client declaration. Typically it isn't finished.
●Server demonstrates end of Server_hello.
Stage 3 − Client confirmation and key trade.
●Client sends testament, provided that mentioned by the server.
●It additionally sends the Pre-ace Mystery (PMS) encoded with the server's public key.
●Client likewise sends Certificate_verify message in the event that authentication is sent by him to demonstrate he has the confidential key related with this declaration. Essentially, the client signs a hash of the past messages.
Stage 4 − Finish.
SSL Meeting Foundation Phase4
●Client and server send Change_cipher_spec messages to one another to cause the forthcoming code state to be duplicated into the present status.
●From here onward, all information is encoded and uprightness secured.
●Message "Wrapped up" from each end checks that the vital trade and verification processes were effective.
Each of the four stages, talked about above, occur inside the foundation of TCP meeting. SSL meeting foundation begins after TCP SYN/SYNACK and wraps up before TCP Balance.
Continuing a Separated Meeting
●It is feasible to continue a separated meeting (through Alertmessage), on the off chance that the client sends a hello_request to the server with the encoded session_id data.
●The server then, at that point, decides whether the session_id is legitimate. Whenever approved, it trades ChangeCipherSpec and completed messages with the client and secure correspondences continue.
●This tries not to recalculate of meeting figure boundaries and recoveries registering at the server and the client end.
SSL Meeting Keys
We have seen that during Stage 3 of SSL meeting foundation, a pre-ace mystery is sent by the client to the server encoded utilizing server's public key. The expert mystery and different meeting keys are created as follows −
●The expert mystery is created (by means of pseudo irregular number generator) utilizing −
○The pre-ace mystery.
○Two nonces (RA and RB) traded in the client_hello and server_hello messages.
●Six mystery values are then gotten from this expert mystery as −
○Secret key utilized with Macintosh (for information sent by server)
○Secret key utilized with Macintosh (for information sent by client)
○Secret key and IV utilized for encryption (by server)
○Secret key and IV utilized for encryption (by client)
TLS Convention
To give an open Web standard of SSL, IETF delivered The Vehicle Layer Security (TLS) convention in January 1999. TLS is characterized as a proposed Web Standard in RFC 5246.
Striking Elements
●TLS convention has same targets as SSL.
●It empowers client/server applications to impart in a safe way by confirming, forestalling listening in and opposing message change.
●TLS convention sits over the solid association situated transport TCP layer in the systems administration layers stack.
●The design of TLS convention is like SSLv3 convention. It has two sub conventions: the TLS Record convention and the TLS Handshake convention.
●However SSLv3 and TLS convention have comparable design, a few changes were made in engineering and working especially for the handshake convention.
Examination of TLS and SSL Conventions
There are fundamental eight contrasts among TLS and SSLv3 conventions. These are according to the accompanying −
Convention Variant − The header of TLS convention section conveys the form number 3.1 to separate between number 3 conveyed by SSL convention portion header.
●Message Validation − TLS utilizes a keyed-hash message verification code (H-Macintosh). Benefit is that H-Macintosh works with any hash capability, not simply MD5 or SHA, as unequivocally expressed by the SSL convention.
●Meeting Key Age − There are two contrasts among TLS and SSL convention for age of key material.
●Strategy for figuring pre-endlessly ace insider facts is comparative. Yet, in TLS convention, calculation of expert mystery utilizes the HMAC standard and pseudorandom capability (PRF) yield rather than specially appointed Macintosh.
○The calculation for figuring meeting keys and commencement values (IV) is unexpected in TLS in comparison to SSL convention.
●Ready Convention Message −
○TLS convention upholds every one of the messages utilized by the Ready convention of SSL, aside from No testament ready message being made repetitive. The client sends void declaration on the off chance that client confirmation isn't needed.
○Numerous extra Alarm messages are remembered for TLS convention for other mistake conditions, for example, record_overflow, decode_error and so on.
●Upheld Code Suites − SSL upholds RSA, Diffie-Hellman and Fortezza figure suites. TLS convention upholds all suits with the exception of Fortezza.
●Client Endorsement Types − TLS characterizes testament types to be mentioned in a certificate_request message. SSLv3 support these. Also, SSL support specific different sorts of declaration like Fortezza.
●CertificateVerify and Completed Messages −
○In SSL, complex message method is utilized for the certificate_verify message. With TLS, the checked data is contained in the handshake messages itself hence staying away from this complicated methodology.
○Completed message is processed in various habits in TLS and SSLv3.
●Cushioning of Information − In SSL convention, the cushioning added to client information before encryption is the base sum expected to make the complete information size equivalent to a various of the code's block length. In TLS, the cushioning can be any sum that outcomes in information size that is a various of the code's block length, up to 255 bytes.
The above distinctions among TLS and SSLv3 conventions are summed up in the accompanying table.
Read more: what is security | what is security governance | what is abbreviation | abbreviation
Secure Perusing - HTTPS
In this part, we will examine the utilization of SSL/TLS convention for performing secure web perusing.
HTTPS Characterized
Hyper Text Move Convention (HTTP) convention is utilized for web perusing. The capability of HTTPS is like HTTP. The main contrast is that HTTPS gives "secure" web perusing. HTTPS represents HTTP over SSL. This convention is utilized to give the encoded and confirmed association between the client internet browser and the site
The protected perusing HTTPS guarantees that the accompanying substance are encoded −
●URL of the mentioned page.
●Page contents given by the server to the client.
●Items in structures filled in by client.
●Treats laid out in the two headings.
Working of HTTPS
HTTPS application convention regularly utilizes one of two famous vehicle layer security conventions - SSL or TLS. The course of secure perusing is portrayed in the accompanying focuses.
●You demand a HTTPS association with a page by entering https://followed by URL in the program address bar.
●Internet browser starts an association with the web server. Utilization of https summons the utilization of SSL convention.
●An application, program for this situation, utilizes the framework port 443 rather than port 80 (utilized in the event of http).
●The SSL convention goes through a handshake convention for laying out a solid meeting as examined in before segments.
●The site at first sends its SSL Computerized declaration to your program. On check of declaration, the SSL handshake advances to trade the common mysteries for the meeting.
●When a believed SSL Computerized Testament is utilized by the server, clients get to see a lock symbol in the program address bar. At the point when a Lengthy Approval Declaration is introduced on a site, the location bar becomes green.
●When laid out, this meeting comprises of many secure associations between the web server and the program.
Utilization of HTTPS
●Utilization of HTTPS gives secrecy, server confirmation and message uprightness to the client. It empowers safe lead of web based business on the Web.
●Keeps information from listening in and denies data fraud which are normal assaults on HTTP.
Present day internet browsers and web servers are outfitted with HTTPS support. The utilization of HTTPS over HTTP, notwithstanding, requires seriously figuring power at the client and the server end to complete encryption and SSL handshake.
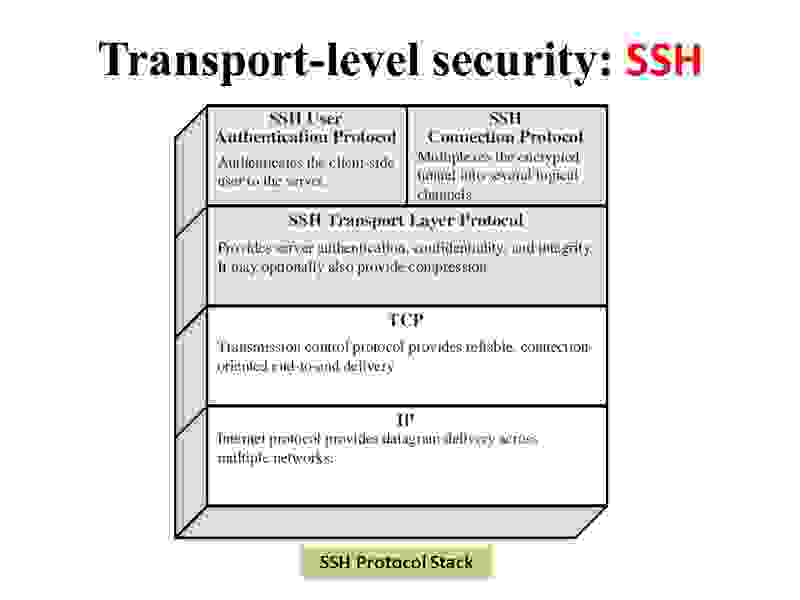
Secure Shell Convention (SSH)
The remarkable elements of SSH are as per the following −
●SSH is an organization convention that sudden spikes in demand for top of the TCP/IP layer. It is intended to supplant the TELNET which gave unstable method for remote logon office.
●SSH gives a protected client/server correspondence and can be utilized for undertakings, for example, record move and email.
●SSH2 is a predominant convention which gives further developed network correspondence security over prior rendition SSH1.
SSH Characterized
SSH is coordinated as three sub-conventions.
SSH Characterized
●Transport Layer Convention − This piece of SSH convention gives information secrecy, server (have) validation, and information uprightness. It might alternatively give information pressure too.
○Server Confirmation − Host keys are lopsided like public/confidential keys. A server utilizes a public key to demonstrate its personality to a client. The client checks that reached server is a "known" have from the information base it keeps up with. When the server is confirmed, meeting keys are created.
○Meeting Key Foundation − After validation, the server and the client concur upon code to be utilized. Meeting keys are created by both the client and the server. Meeting keys are produced before client confirmation so that usernames and passwords can be sent scrambled. These keys are by and large supplanted at normal stretches (say, consistently) during the meeting and are obliterated following use.
○Information Trustworthiness − SSH utilizes Message Confirmation Code (Macintosh) calculations to for information honesty check. It is an improvement more than 32 digit CRC utilized by SSH1.
●Client Confirmation Convention − This piece of SSH validates the client to the server. The server checks that entrance is given to expected clients as it were. Numerous confirmation strategies are presently utilized, for example, composed passwords, Kerberos, public-key verification, and so on.
●Association Convention − This gives various coherent channels over a solitary hidden SSH association.
SSH Administrations
SSH offers three principal types of assistance that empower arrangement of many secure arrangements. These administrations are momentarily depicted as follows −
●Secure Order Shell (Far off Logon) − It permits the client to alter records, view the items in catalogs, and access applications on associated gadget. Frameworks heads can remotely begin/view/stop administrations and cycles, make client records, and change document/catalogs consents, etc. All errands that are doable at a machine's order brief can now be performed safely from the remote machine utilizing secure remote logon.
●Secure Document Move − SSH Record Move Convention (SFTP) is planned as an expansion for SSH-2 for secure record move. Basically, it is a different convention layered over the Safe Shell convention to deal with document moves. SFTP scrambles both the username/secret phrase and the document information being moved. It involves a similar port as the Safe Shell server, for example framework port no 22.
●Port Sending (Burrowing) − It permits information from unstable TCP/IP based applications to be gotten. After port sending has been set up, Secure Shell reroutes traffic from a program (typically a client) and sends it across the scrambled passage to the program on the opposite side (normally a server). Various applications can communicate information over a solitary multiplexed secure channel, disposing of the need to open many ports on a firewall or switch.
Benefits and Limits
The advantages and limits of utilizing correspondence security at transport layer are as per the following −
1.Benefits
●Transport Layer Security is straightforward to applications.
●Server is verified.
●Application layer headers are covered up.
●It is more fine-grained than security components at layer 3 (IPsec) as it works at the vehicle association level.
2.Limits
●Relevant to TCP-based applications just (not UDP).
●TCP/IP headers are in clear.
●Appropriate for direct correspondence between the client and the server. Doesn't cook for secure applications utilizing chain of waiters (for example email)
●SSL doesn't give non-disavowal as client confirmation is discretionary.
●If necessary, client confirmation should be carried out above SSL.
Synopsis
An enormous number of web applications have arisen on the Web in the previous 10 years. Numerous e-Administration and internet business gateway have come on the web. These applications expect that meeting between the server and the client is secure giving secrecy, validation and trustworthiness of meetings.
One approach to moderating an expected assault during a client's meeting is to utilize a protected correspondence convention. Two of such correspondence conventions, Secure Attachments Layer (SSL) and Transport Layer Security (TLS), are examined in this part. Both of these convention capability at Transport layer.
One more vehicle layer convention, Secure Shell (SSH), intended to supplant the TELNET, gives secure method for remote logon office. It is fit for offering different types of assistance, for example, Secure Order Shell and SFTP.
Work of Transport layer security has many advantages. In any case, the security convention planned at these layer can be utilized with TCP as it were. They don't give security to correspondence carried out utilizing UDP.